Notes about 802.1x and MAC authentication
Open network ports in offices, waiting rooms and entrance halls make me curious. Sometimes I want to plugin a network cable, just to see if I get an IP address. I know many companies that does not care about network access control. Anybody can plugin any device to the network. When talking with customers about network access control, or port security, I often hear their complains about complexity. It’s too complex to implement, to hard to administrate. But it is not sooo complex. In the easiest setup (with mac authentication), you need a switch, that can act as authenticator, and a authentication server. But IEEE 802.1x is not much more complicated.
A brief overview over IEEE 802.1x
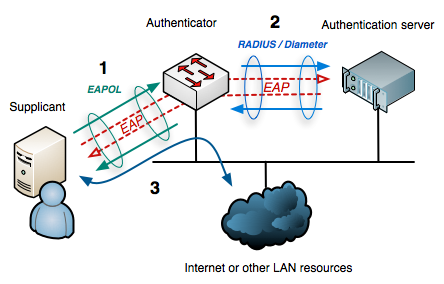
IEEE 802.1X offers authentication and authorization in wired or wireless networks. The supplicant (client) requests access to the network by providing a username/ password, or a digital certificate to the authenticator (switch). The authenticator forwards the provided credentials to the authentication server (mostly RADIUS or DIAMETER). The authentication server verifies the credentials and decides, if the supplicant is allowed to access the network.
802.1x uses the Extensible Authentication Protocol (EAP RFC5247) for authentication. Because EAP is a framework, there are different implementations, like EAP Transport Layer Security (EAP-TLS), or EAP with pre-shared key (EAP-PSK). Because it is only a framework, each protocol, that uses EAP, has to encapsulate it. Typical encapsulations are EAP over LAN (that is what 802.1x uses), RADIUS/ DIAMETER can use also use EAP. Protected EAP (PEAP) encapsulates EAP traffic into a TLS tunnel. PEAP is typically used as a replacement for EAP in EAPOL, or with with RADIUS or DIAMETER.
Patrick Terlisten/ vcloudnine.de/ Creative Commons CC0
So far nothing special. It’s more a security thing, but an important one, if you ask me. But many customers avoid 802.1x, because of complexity. It’s perfect to keep you out of your own network, if something fails. And not all devices can act as supplicant.
But there is another benefit of 802.1x: RADIUS-Access-Accept messages can be used to dynamically assign VLAN memberships (RADIUS Extensions, RFC6929). To assign a VLAN membership to a port, to which a supplicant is connected, the RADIUS server adds three attributes to the Access-Accept message:
- Tunnel-Type (VLAN)
- Tunnel-Medium-Type (802)
- Tunnel-Private-Group-Id (VLAN ID)
The authenticator uses these attributes to dynamically assign a VLAN to the port, to which the supplicant is connected.
MAC authentication
How does MAC authentication fit into this? If a client does not support 802.1x, the authenticator can use the mac-address of the connected device as username and password. The RADIUS server can use these credentials to authenticate the connected device. If you use a windows-based NAP (Windows Server NPS role), you have to create a user object in your Active Directory or local user database, that uses the mac-address as username and password. Depending on the switch configuration, the format of the username differes (xx:xx:xx:xx:xx:xx or xxxxxx-xxxxxx etc.). It’s a security fail, right? Yes, it is. So please:
- Use MAC authentication only when needed, and
- make sure that your authenticator uses PEAP
PEAP uses a TLS tunnel to protect the CHAP messages.
Another important part is your authentication server, mostly a RADIUS or DIAMETER server. Make sure that it is highly available. You should have at least two authentication server. I would not load balance them through a load balancer (Citrix NetScaler etc.). Simply add two authentication servers to your switch configuration. If your authentication server uses a user database, like Microsoft Active Directory, make sure that this database is also highly available. As I said: It is perfect to keep you out of your own network.
Sample config for ArubaOS (HPE ProVision based switches)
Here’s a sample config for a Aruba 2920 switch, running ArubaOS WB.16.04. 802.1x and MAC authentication are configured for the ports 1 to 5. If the authentication failes, VLAN 999 will be assigned to the port. VLAN 999 is used as unauth VLAN, which is used for unauthenticated clients.
radius-server host 192.168.1.10 key "T0p5ecr3t"
radius-server host 192.168.1.11 key "T0p5ecr3t"
aaa authentication port-access eap-radius
aaa authentication mac-based peap-mschapv2
aaa port-access authenticator 1-5
aaa port-access authenticator 1 client-limit 32
aaa port-access authenticator 2 client-limit 32
aaa port-access authenticator 3 client-limit 32
aaa port-access authenticator 4 client-limit 32
aaa port-access authenticator 5 client-limit 32
aaa port-access authenticator active
aaa port-access mac-based 1-5
aaa port-access mac-based 1 addr-limit 32
aaa port-access mac-based 1 unauth-vid 999
aaa port-access mac-based 2 addr-limit 32
aaa port-access mac-based 2 unauth-vid 999
aaa port-access mac-based 3 addr-limit 32
aaa port-access mac-based 3 unauth-vid 999
aaa port-access mac-based 4 addr-limit 32
aaa port-access mac-based 4 unauth-vid 999
aaa port-access mac-based 5 addr-limit 32
aaa port-access mac-based 5 unauth-vid 999
If 802.1x fails, the authenticator, will try MAC authentication. If this fails too, VLAN 999 is assigned to the switch port.
In this case, the client was authenticated by 802.1x.
SW1(config)# show port-access auth client 1 detailed
Port Access Authenticator Client Status Detailed
Port-access authenticator activated [No] : Yes
Allow RADIUS-assigned dynamic (GVRP) VLANs [No] : No
Dot1x2010 Mode [Disabled] : Disabled Use LLDP data to authenticate [No] : No
Client Base Details :
Port : 1
Client Status : Authenticated Session Time : 9 seconds
Client name : user@domain Session Timeout : 0 seconds
IP : n/a MAC Address : 643150-7c7c9f
Access Policy Details :
COS Map : Not Defined In Limit Kbps : Not Set
Untagged VLAN : 2500 Out Limit Kbps : Not Set
Tagged VLANs : No Tagged VLANs
Port Mode : 1000FDx
RADIUS ACL List : No Radius ACL List
This is the output for MAC authentication.
SW1(config)# show port-access mac-based clients 1 detailed
Port Access MAC-Based Client Status Detailed
Client Base Details :
Port : 1
Client Status : authenticated Session Time : 14 seconds
MAC Address : 643150-7c7c9f Session Timeout : 0 seconds
IP : n/a
Access Policy Details :
COS Map : Not Defined In Limit Kbps : Not Set
Untagged VLAN : 1 Out Limit Kbps : Not Set
Tagged VLANs : No Tagged VLANs
Port Mode : 1000FDx Auth Mode : User-based
RADIUS ACL List : No Radius ACL List
In both cases, VLAN 1 was dynamically assigned by RADIUS-Access-Accept messages.
