Setting up split DNS using Windows DNS server
Sometimes it’s necessary to have two DNS servers that are authoritative for the same DNS namespace. This is the case if you use the same namespace for your web site and your internal Active Directory domain, e.g. terlisten-consulting.de. Or that you have created the zone terlisten-consulting.de in your Windows DNS to point specific hosts to internal IP addresses. The DNS servers at your ISP would be authoritative, and the domain controllers of your Active Directory would also be authoritative for the same domain. The response to a query depends on which DNS server you ask. So what would happen if you try to resolve www.terlisten-consulting.de, and the internal DNS has no record for it?
C:\Users\Administrator.LAB>nslookup www.terlisten-consulting.de
Server: adc1.lab.local
Address: fdda:28ad:487:3::1
*** adc1.lab.local can't find www.terlisten-consulting.de: Non-existent domain
In this case, the domain controller in my lab is authoritative for terlisten-consulting.de. But he doesn’t has a A record for www.terlisten-consulting.de. If I remove the zone from my domain controller, or if I use an external DNS server, I get a non-authoritative answer.
C:\Users\Administrator.LAB>nslookup www.terlisten-consulting.de
Server: adc1.lab.local
Address: fdda:28ad:487:3::1
Non-authoritative answer:
Name: waws-prod-am2-015.cloudapp.net
Address: 23.100.1.29
Aliases: www.terlisten-consulting.de
azr-terlistenconsulting.azurewebsites.net
waws-prod-am2-015.vip.azurewebsites.windows.net
This, the same DNS namespace on different DNS server, is called “split DNS” (sometimes also called split-horizon DNS, split-view DNS or split-brain DNS).
Do it right
Split DNS is pretty handy, and sometimes it’s necessary. When it comes to Microsoft Exchange, it a common practice to use the same external DNS namespace for the internal and external URLs. This requires, that I create a zone for the externally used DNS namespace on my internal DNS (in most cases: Microsoft Windows Activice Directory domain controllers). The downside: I must create all DNS entries on my internal DNS, and I must point them to their external IP addresses, except the ones that should point to an internal IP.
| FQDN | Internal/ External IP address |
|---|---|
| www.terlisten-consulting.de | external IP address |
| exchange.terlisten-consulting.de | internal IP address |
| shop.terlisten-consulting.de | external IP address |
Otherwise, users that use the domain controllers as DNS server, wouldn’t be able to resolve www or shop. This is challenging. But there’s a solution.
Create split DNS for single hosts
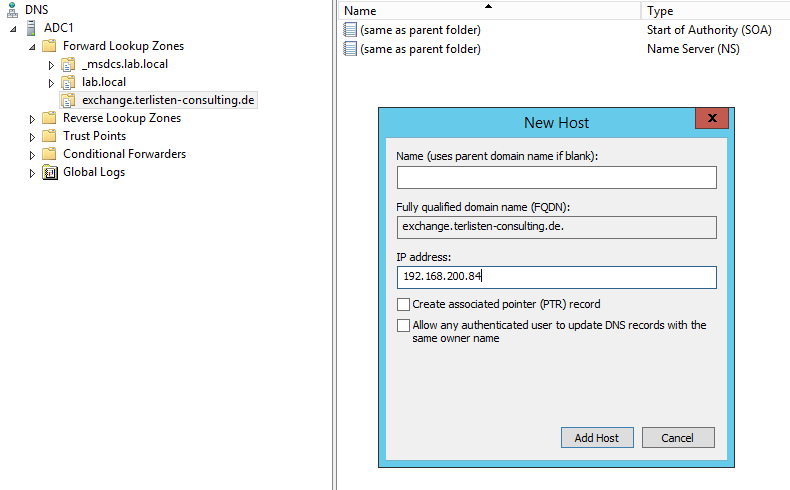
The Domain Name System is hierarchy organized. Because of this, I can tell my DNS server to be authoritative only for a sub-tree of a domain, e.g. exchange.terlisten-consulting.de. If I try to resolve www.terlisten-consulting.de, the DNS server would go down the hierarchy starting at the DNS root servers (or it would ask a forwarder). Instead of creating a zone for the whole namespace, create a zone for the host. Simply add
- a new primary zone
- don’t allow dynamic updates to the zone, and
- create a new A or AAAA record for the host
Make sure
- to leave the name field empty
- don’t create a PTR record
- point it to the internal IP of the host
Patrick Terlisten/ vcloudnine.de/ Creative Commons CC0
A simple nslookup will show if split DNS works as expected.
C:\Users\Administrator.LAB>nslookup www.terlisten-consulting.de
Server: adc1.lab.local
Address: fdda:28ad:487:3::1
Non-authoritative answer:
Name: waws-prod-am2-015.cloudapp.net
Address: 23.100.1.29
Aliases: www.terlisten-consulting.de
azr-terlistenconsulting.azurewebsites.net
waws-prod-am2-015.vip.azurewebsites.windows.net
C:\Users\Administrator.LAB>nslookup exchange.terlisten-consulting.de
Server: adc1.lab.local
Address: fdda:28ad:487:3::1
Name: exchange.terlisten-consulting.de
Address: 192.168.200.84
Works as expected. Make sure to clear the DNS server cache after you have added the zones.
Windows DNS Server Policies
Windows Server 2016 will introduce Windows DNS Server Policies. DNS Policies will allow you to control how a DNS Server handles answers to queries based on parameters like source IP address, IP address of the network interface that has received the query etc. In future, DNS Server Policies can be used to configure split DNS.
