Trouble due to changed vDS default security policy
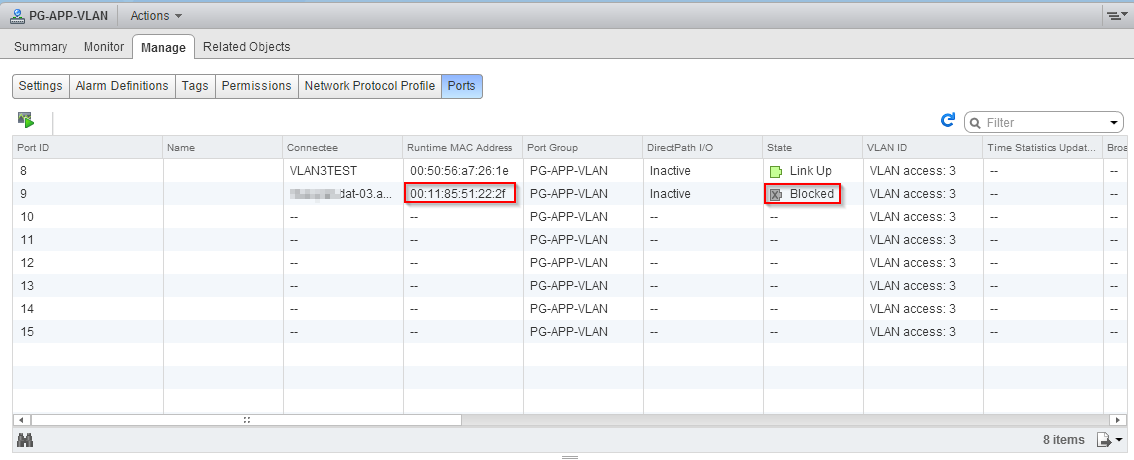
A customer contacted me, because he had trouble to move a VM between two clusters. The hosts in the source cluster used vNetwork Standard Switches (vSS), the hosts in the destination cluster vNetwork Distributed Switch (dVS). Because of this, a host in the destionation cluster had an additional vSS with the same port groups, that were used in the source cluster. This configuration allowed the customer to do vMotion without shared storage between the two clusters. The setup worked fine, until the customer moved a specific VM to the new cluster and switched the port group of the VM from the vSS to the vDS: The VM lost the connect to the network. A switch back to the vSS restored network connectivity for the VM. While troubleshooting this issue I noticed that the port was blocked due to a L2 security violation.
Patrick Terlisten/ vcloudnine.de/ Creative Commons CC0
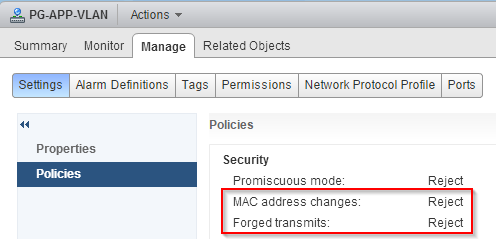
If you take a closer look at the mac-address of the VM with the blocked port, you will notice, that it differs from the usually used range of mac-addresses. Now VMware KB2030982 comes into play. It describes a change to the default security policy for vDS distributed port groups. This table was taken from VMware KB2030982 and shows the differences between the security settins.
| Default Setting | vSphere v5.0 and earlier | vSphere v5.1 and later |
|---|---|---|
| Promiscuous Mode | Reject | Reject |
| MAC Address Changes | Accept | Reject |
| Forged Transmit | Accept | Reject |
Patrick Terlisten/ vcloudnine.de/ Creative Commons CC0
But why was the VM hit by this change? The VM is the result of a P2V migration and it’s running an application, that relies on a specific mac-address. Because of this, the mac-address of the old physical server was entered in the network driver properties. The changed security settings prevent the usage of forged mac-addresses. The host compares the source mac-address being transmitted by the OS with the effective mac-address for its adapter to see if they match. If not, the hosts drops the packet. To allow the usage of forged mac-addresses, the security settings “Forged transmits”, and optional, “MAC address changes” needs to be changed from “Reject” to “Accept”. You can modify these settigns per port group and there is no need to change it for all port groups of a dVS.
